Can we block LDAP port 389 via a Network Firewall between AD Domain Members and AD Domain controller? This lab scenario is a test to find out what happens when we block Port 389 and what actually goes on between a domain member and a domain controller.
Summary
The object was to see if LDAPS/636 can be enforced by blocking LDAP/389 in any way for communication between AD DC and members. And the conculusion that no, it is not possible to keep the domain trust alive while blocking LDAP-TCP/389 and CLDAP-UDP/389 from Network Firewall. However, simple bind over unencrypted LDAP/389 channel can be prevented via registry settings on the DC.
General Topology
Network Topology
Three Zones will be configured on the Network Firewall, two of these will be of relevance in this lab.
- Zone 1 - WAN (Management) - This zone will be used to connect to the virtual firewall with web interface, no traffic will be allowed to this zone from any other zone. This is purely for management.
- Zone 2 - Services - This zone will host AD Domain Controller and Certificate Authority VMs
- Zone 3 - Applications - This zone will host a sample Application Server that will be joined to the Active Directory domain
---Image Placeholder---
Servers Setup
- DC01 (192.168.1.2) - Configured with Active Directory Domain Services role, serves as the Primary Domain Controller for this AD Domain. This will also be the primary DNS server. (Setting up AD is not covered in this article, default setup is enough. Just create a non-default Domain Admin account.)
- CA01 (192.168.1.3) - Configured with Active Directory Certificate Services role, serves as the primary Certificate Authority for this AD Domain. (Setting up AD is not covered in this article, default setup is enough.)
- AP01 (192.168.2.2) - A blank server in a different subnet, this is the server where the domain communication tests will be performed.
Basic Domain Controller Setup
We'll setup a baseline policy for all domain members to allow remote management from the DC and enroll certificates from the CA.
Following inbound firewall rules are required for remote management:
COM+ Network Access (DCOM-In)
Remote Event Log Management (RPC-EMAP)
Remote Event Log Management (NP-In)
Remote Event Log Management (RPC)
We will add this to the Default Domain Policy, but you can create a custom policy and link it as necessary.
This can be done via GUI but I have done it via PowerShell out of curiosity.
$Domain = 'zones.ad'
$GpoName = 'Default Domain Policy'
$PStore = "$Domain\$GpoName"
Get-NetFirewallRule -DisplayGroup "Remote Event Log Management" -Direction Inbound | Copy-NetFirewallRule -NewPolicyStore $PStore
Get-NetFirewallRule -DisplayName ComPlusNetworkAccess-DCOM-In -Direction Inbound | Copy-NetFirewallRule -NewPolicyStore $PStore
Set-NetFirewallRule -PolicyStore $PStore -DisplayGroup "Remote Event Log Management" -Enabled True -Action Allow
Set-NetFirewallRule -PolicyStore $PStore -DisplayName ComPlusNetworkAccess-DCOM-In -Enabled True -Action Allow
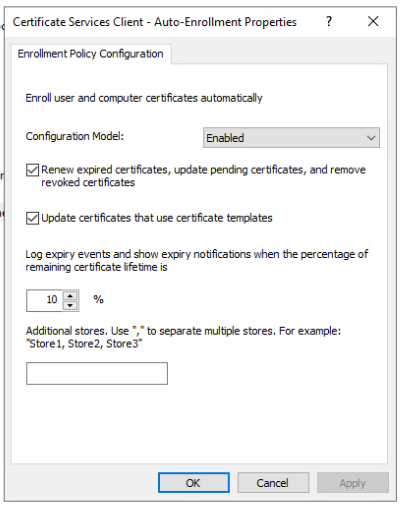
To enable Certificate Auto-Enrollment from CA, Certificate Services Client - Auto-Enrollment Properties need to be set as Enabled. Check "Renew Expired Certificates" and "Update certificates that use template" as well.
This is located under Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Public Key Policies
Run gupdate /force on DC and CA to apply the new policy, this will enable LDAPS on DC and Remote Management capability on member servers.
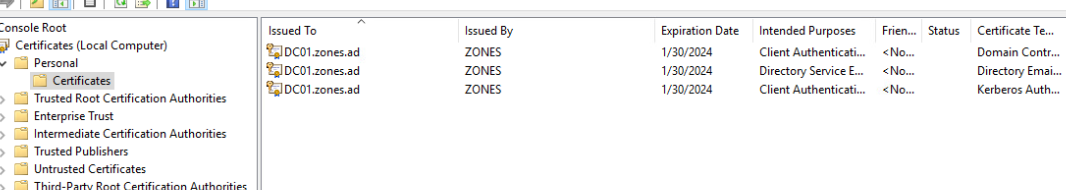
You can now see the certificates in the DC Computer Personal Store. It is recommended to apply this GPo via Default Domain Controllers Policy in production domains along with an enhanced Kerberos template.
Verify LDAPS Reachability
Run LDP.EXE on the DC itself and click on Connection -> Connect
Use Server Hostname as the Sever, Port 636 and check SSL and click OK.
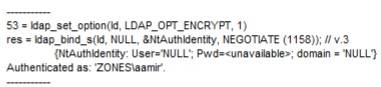
If LDAPS is working, you will get the following output (along with other parameters, but this is what we care about)
Host supports SSL, SSL cipher strenght = 256 bits
Established connection to dc01
Attempt to bind to this connection, Ctrl+B then OK. (Bind as currently logged on user). You should be able to connect.